Skip The Pipeline Scan Docker Images Locally with Trivy
Resolve your container vulnerabilities before pushing your code!
September 27, 2024

Trivy has become an industry leading tool to secure your containers.
1. Overview
We often unknowingly include vulnerabilities in our containers through the base image. Ergo, scanning the direct dependencies of our source code is not enough when we deploy our application by way of containerization.
One is likely to see Trivy scans executed in the CI pipeline. In this case, one must push changes and wait for the Trivy scan to execute in the pipeline before verifying that the vulnerabilities have been resolved. However—if the vulnerabilities were not resolved—one would have to repeat this process repeatedly in an inefficient cycle until all the vulnerabilities are resolved.
We can shift this process left by doing everything locally before pushing the code. In this guide, I will show you how to build and scan Docker images locally with Trivy before pushing your code.
2. Build the Docker Image
If you have already built the image you want to scan, then skip to the next step. To build your Docker image, leverage your IDE plugin of choice or open a terminal and run the following:
$ docker build . -t my-docker-image:latestHere's a breakdown of each part of this command:
- docker build . will build my Docker image based on the Dockerfile located at the root of my working directory.
- -t my-docker-image:latest will create my image with the name "my-docker-image" and the tag "latest".
3. Execute the Trivy Scan Locally
Leverage your IDE plugin of choice or type the following in the terminal:
$ docker run --rm -v /var/run/docker.sock:/var/run/docker.sock aquasec/trivy:latest image my-docker-image:latestHere's a breakdown of each part of this command:
- docker run --rm runs the container and automatically removes it when it exits. We don't need the container to persist after the scan finishes.
- -v /var/run/docker.sock:/var/run/docker.sock will mount the Docker socket to the container. This allows us to pass our local images to the Trivy container for scanning. Note: If the image you want to scan is in a public repository, you can omit mounting the Docker socket and provide the full endpoint for the image (i.e. docker.io/library/nginx:latest).
- image my-docker-image:latest is the image that I just built in the previous step to be scanned.
4. View the Results
The results of the scan will show in the same terminal. Now you can verify if vulnerabilities were resolved before pushing your changes to the pipeline!
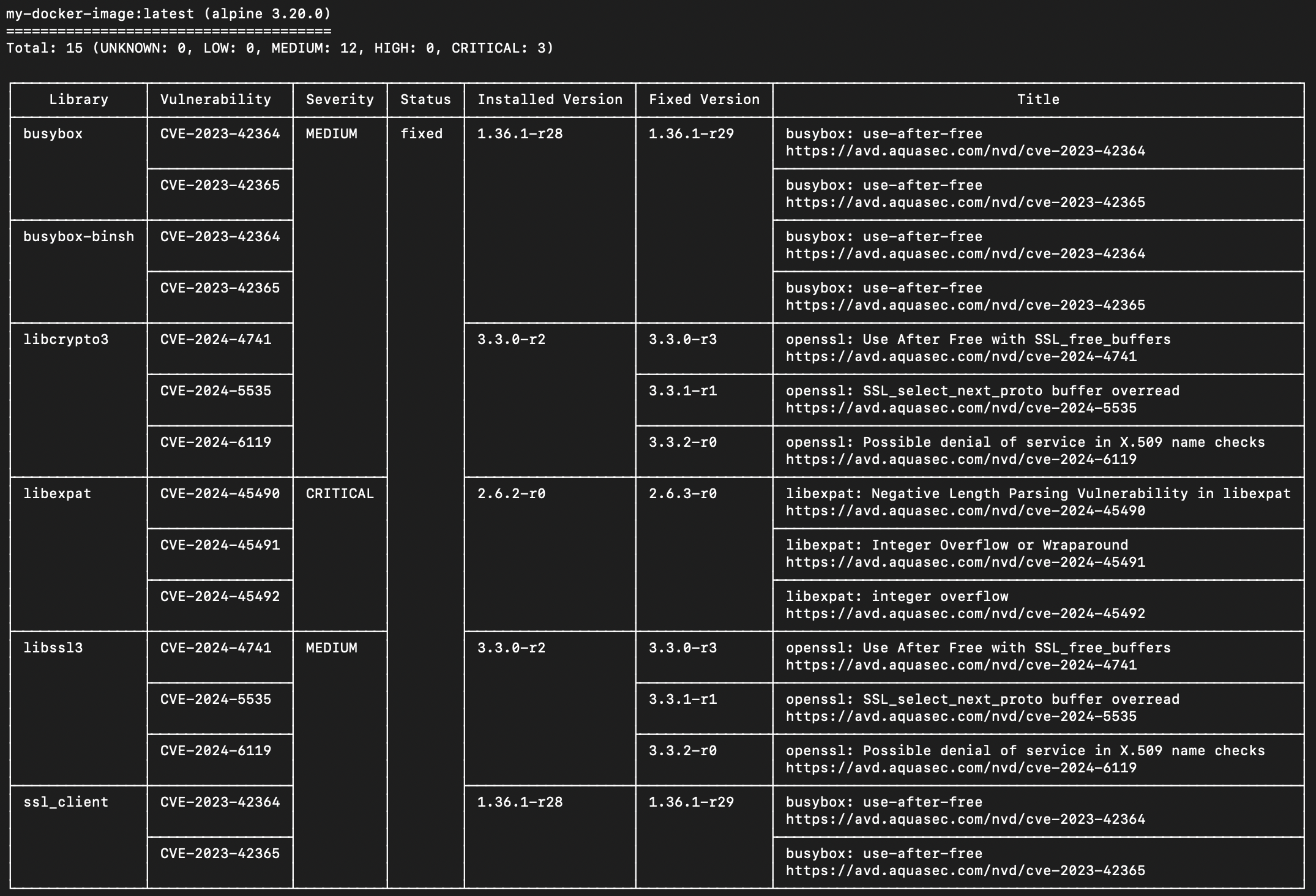
Trivy outputs a nicely formatted table with the results of the vulnerability scan.
If some vulnerabilities remain and can be resolved, you can continue to make changes and repeat the above locally before pushing to the pipeline. This cycle is much more efficient rather than using the pipeline to verify remediation.
And that's it! Make sure to choose lightweight base images to lessen the chances of packaging vulnerabilities with your container. To learn more about securing images, I've found the OWASP guidance particularly helpful: OWASP Developer Guide: Container Security.
© 2023-2026 Developed by Fernando Sesma
